When designing a solution, you want to be sure that your communications are secure and that your users can trust your application. Typically, SSL certificates can be useful for this purpose.That is well and good from a design and development perspective, but there may some management headaches when operating and governing the solution. How do you keep track of the certificates? How do you guarantee that they are kept secure? How do you ensure that certificates renew on time?
Azure Key Vault helps safeguard cryptographic keys and secrets used by cloud applications and services. It streamlines the key management process, enabling you to maintain control of keys that access and encrypt your data. Developers can create keys for development and testing in minutes, and then seamlessly migrate them to production keys. Security administrators can grant (and revoke) permission to keys, as needed.
When designing a solution, you want to be sure that your communications are secure and that your users can trust your application. Typically, SSL certificates can be useful for this purpose.
That is well and good from a design and development perspective, but there may some management headaches when operating and governing the solution. How do you keep track of the certificates? How do you guarantee that they are kept secure? How do you ensure that certificates renew on time?
Azure’s Key Vault can help in this area. Recently, at Microsoft Ignite 2016– The team announced that Azure Key Vault supports management of certificates from supported Certificate Authorities (so far, this includes DigiCert, GlobalSign and WoSign). The process is well-documented. My personal domain name has an SSL validated by DigiCert, so I am going to use the previously linked blog process, and step through the process – showing the output along the way.
1. Firstly, log in to your Azure Account via the Resource Management PowerShell cmdlets. Double check which subscriptions you have access to, and that you have set a default subscription context.
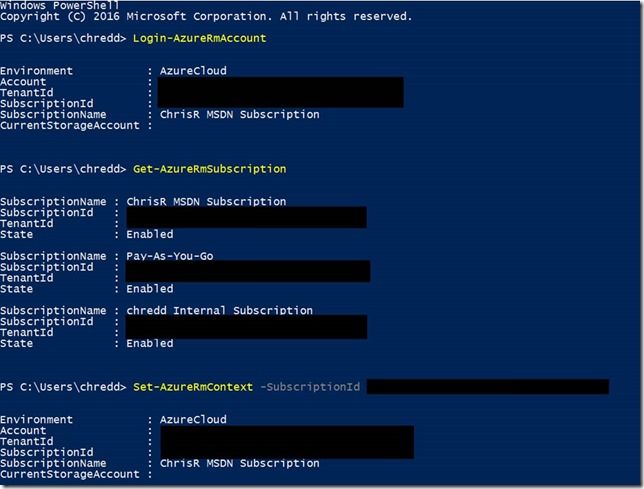
2. Set variables for $vaultName, $resourceGroupName and $Location and use the command New-AzureRmKeyVault -VaultName $vaultName -ResourceGroupName $resourceGroupName -Location $location to create an Azure Key Vault, if you do not have one. As you can see in the screenshot below, my key vault already exists.
3. Now that you have an Azure Key Vault, you need to link this to your organisation for your Certificate Authority issuer. There are a few pieces of information needed to get this going. Specifically, for DigiCert, you can find this here.
a. $orgIdentifier – The organisation ID associated with your CertCentral account on DigiCert.
b. $apiKey – You need to create an API Key through DigiCert CertCentral interface. The API key is a relatively long alphanumeric string.
c. $accountId – This is the ID of your DigiCert account.
d. $issuerName – Something that makes sense to you, for the issuer of your certificate with the Certificate Authority. In my case, I have used DigiCert and my initials, as it relates to my personal domain.
Finally, use the Set-AzureKeyVaultCertificateIssuer cmdlet with the associated parameters in the image below to ensure the Certificate Issuer is associated with your KeyVault account.
NOTE: These steps differ depending on your certificate authority. You should check these out on the Key Vault blog here, for either GlobalSign or WoSign.

4. Now that we have created the link to the issuer, we should create a certificate policy. The policy focuses on the information included in the certificate, when to renew it, and details on the Certificate Authority where the renewal takes place. Below, you can see that I have provided details for a wildcard to my personal domain name, that the certificate should be valid for 12 months and should be renewed 60 days before expiry.
5. Now use the details from the above policy, to create a certificate in the Key Vault. The CertificateName parameter (in my case, $certificateName) is the name of the certificate object as held in the Key Vault, not the name of the certificate with your Certificate Authority.
6. Once you have completed this step, you have submitted a request to DigiCert for the certificate, containing the details of the policy that you created earlier. You can check on the progress by using the cmdlet Get-AzureKeyVaultCertificateOperation, passing in a parameter for VaultName and CertificateName (e.g. as shown below). You can also see that the request has appeared in your DigiCert CertCentral account.
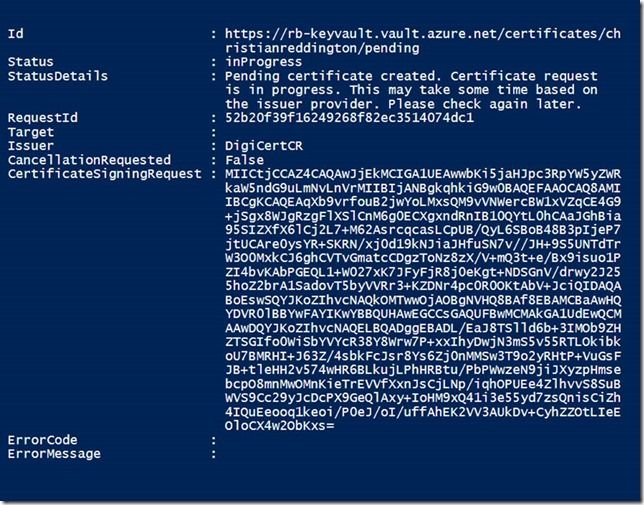
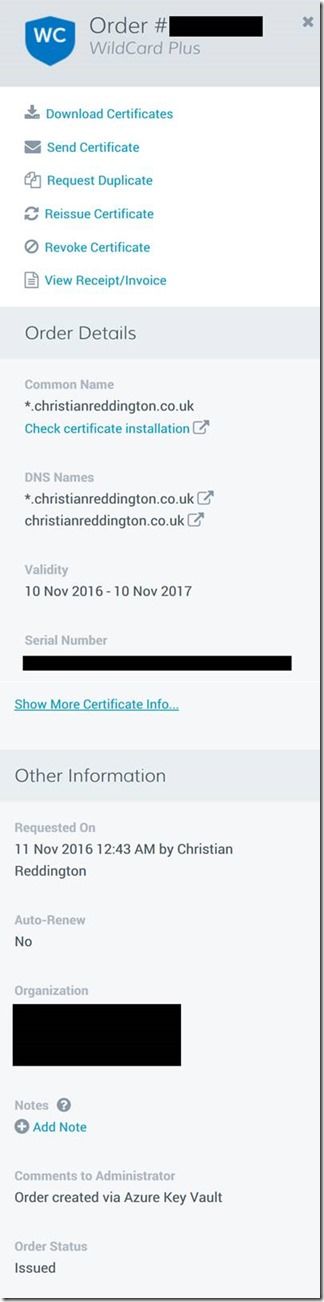
7. You may be contacted by the Certificate Authority to validate details of the organisation requesting the certificate or may need additional details for the Certificate Signing Request. Once complete, you can use the Get-AzureKeyVaultCertificate command, passing in the $vaultName and $certificateName parameters, to find the details needed to access the certificate from Key Vault.

Congratulations, you have now generated a certificate, which has been signed by DigiCert via Azure Key Vault. You can now go and use one of the documented ARM templates, to import Key Vault certificates into your resources. For example, see here on using a certificate within Azure Web App.
However, if you are using the Resource Manager API to deploy your certificates from Key Vault to your resources, you need to ensure that the Key Vault Access Policy allows this;
Set-AzureRmKeyVaultAccessPolicy -VaultName $vaultName -ServicePrincipalName
PS – If you had not spotted it previously, the Azure Key Vault team have an official blog here
PPS – This post bases itself on the blog written by the Key Vault team, here. The aim of this post is to provide a few extra screenshots and focus on the process specifically for DigiCert. I have missed out a few details that are covered by the Key Vault team on certificate renewal. I have also missed out using Key Vault for SSL on Web apps, which are again worth checking out in the blog post referenced above.
Related
If you have been keeping up to date with the latest and greatest in Azure Services (yes, I know there are quite a few!), you may have heard of a new service called Azure Functions. Azure Functions is an event-driven Platform as a Service capability, helping you to execute code upon the occurrence of a particular event. It is currently in preview, though already has a lot of potential.
Blog
In case you had not already heard, Logic Apps have now reached general availability on Azure (or read an MSDN article by Jeff Hollan on the topic).
Blog
Surely, a Hello World post is a right of passage for technical bloggers?
Blog

